Cryptography
Introduction
Have you ever heard about encryption and decryption? These are the techniques which secure your information and data from any unauthorized access and thus maintains the confidentiality. But what these terms mean. Let's discuss one by one and go deep in these terminologies.
Let's start with the title "Cryptography". Let's break this term. Cryptography comprises of two terms - "crypt" and "graphy". Crypt means "hidden" or a "vault" and Graphy stands for "writing". Cryptography is a method of protecting information and communication through some techniques so that only those for whom the information is intended can read and process it. Cryptography
is a very big domain of Networking and Cyber Security. Individuals who
practice this field are known as "Cryptographers".
There are some techniques used to secure your data while transferring from an unsafe network like changing your text into some in-understandable form, merging your words with images also some techniques like microdot.
This picture show how malicious attackers can change your information. For protection from these types of attacks we use cryptography.
What is encryption, decryption?
In today's era of computer-technology, the cryptography is scramble around the encryption and decryption. So, there's a plain text i.e. the ordinary or original text which is intended to send to some receiver. This plain text is converted into some cipher text i.e. the text which is in some in-understandable form. So, at the sender's end this plain text is converted to ciphertext, this practice is known as encryption and at the receiver's end this ciphertext is converted to plain text known as decryption. Encryption and decryption are two opposite terms and are used in cryptography for protecting your information from any malicious attacker and unintended receiver. There's a term key used i.e. key is a string of bits used by a cryptographic
algorithm to transform plain text into cipher text or vice versa. This
key remains private and ensures secure communication.
There's a four objectives of cryptography or we say major concerns of cryptography:
1. Confidentiality : the information cannot be understood by anyone for whom it was unintended.
2. Integrity : the information cannot be altered in storage or transit between sender and intended receiver without the alteration being detected.
3. Non-repudiation : the creator/sender of the information cannot deny at a later stage his or her intentions in the creation or transmission of the information.
4. Authentication : the sender and receiver can confirm each other's identity and the origin/ destination of the information.
Cryptographic Algorithms
Cryptographic system uses some set of procedure or protocols which is implemented with some cryptographic algorithms which includes mathematical algorithms, ciphers to encrypt or decrypt messages. A cipher suite uses one algorithm for encryption, another algorithm for message authentication and another for key exchange. These all algorithms are implemented in network protocols for secure transmission involves public and private key generation for data encryption/decryption.
Cryptography allows senders and receivers to authenticate each other through the use of key pairs.
Various types of Algorithms used in Cryptographic system:
1. Secret Key Cryptography (SKC): Here the only one key is used for both encryption and decryption. This type of encryption is also referred to as symmetric encryption.
2. Public Key Cryptography (PKC): Here two keys are used. This type of encryption is also called
asymmetric encryption. One key is the public key that anyone can access.
The other key is the private key, and only the owner can access it. The
sender encrypts the information using the receiver’s public key. The
receiver decrypts the message using his/her private key. For
non-repudiation, the sender encrypts plain text using a private key,
while the receiver uses the sender’s public key to decrypt it. Thus, the
receiver knows who sent it.
3. Hashing functions: These are different from SKC and PKC. They use no key and are also called one-way encryption. Hash functions are mainly used to ensure that a file remain unchanged. Hash is looks like this :
cfb47e87027d7559a21946edb68b5f7a for message "hello how are you".
cfb47e87027d7559a21946edb68b5f7a for message "hello how are you".
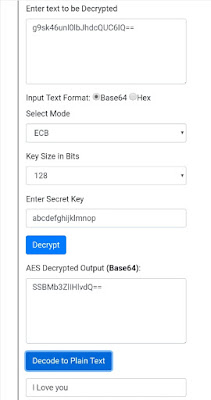
Let's take a small example of encryption:
Let our message be "I Love you" and I want to send it to someone but I don't want it to be altered in transit. So, I will encrypt it with some method. Let method be AES(Advanced Encryption Standard) 128 bit encryption and key be "abcdefghijklmnop". Please don't share your private key with anyone.
After encryption the message is look likes "g9sk46unl0lbJhdcQUC6IQ==" which is completely in-understandable. And at the receiver's end it can be decrypted by that secret key and the message can be read and process.












Awesome explanation bro🤓🤓.
ReplyDeleteTHANKS BROTHER
Delete